Create a reverse shell
This kind of shells can be created either by running an exploit and executng a shellcode that connects back to Exploit Pack or by directly making a binary/py and manually running it in the remote computer, do not confuse this reverse shell with the XSS/VBS/PS agents that even though they also provide a connection back to Exploit Pack there are different because this revese shell are ment to be used as a step-stone to escalate privieleges and run local exploits to pivot to another part of the targeted network during your pentest.
First option more frequently used will be to obtain this shell trough an exploit ( adding it as a shellcode ), but if you wish to to create it manually click on the Reverse shell icon on the toolbar and follow the wizard, select the platform of your choice and click on next, set up the value for Server to the ones you have on your workstation.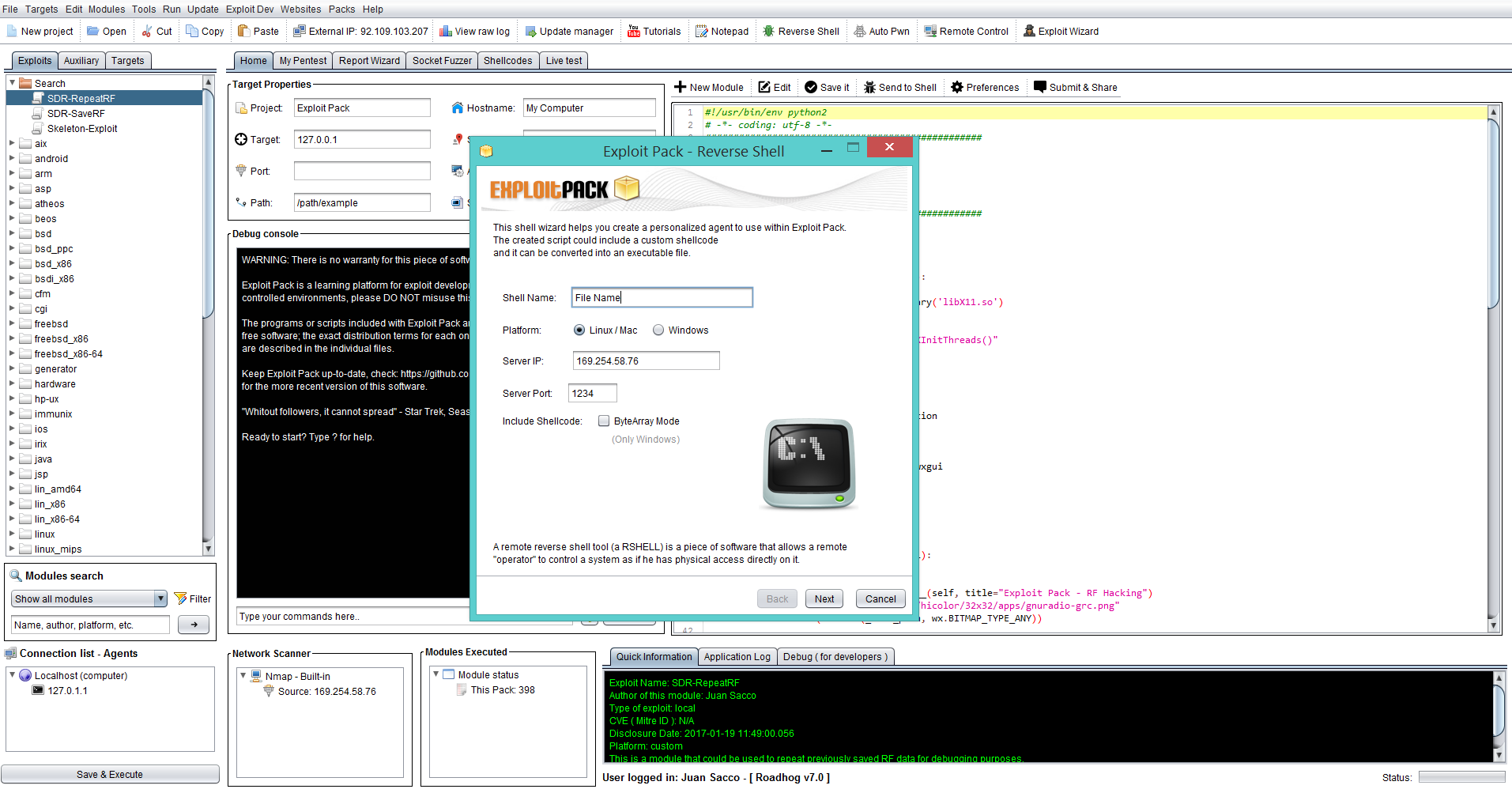
After this is done, you will see the code in Python format, if you need to have a binary we recommend you to use something like Py2Exe http://www.py2exe.org/
