First steps using Exploit Pack
Hey_ new user! _Welcome to Exploit Pack, hopefully this quick guide will take you trough the process of learning this tool.
Enjoy the journey. And hey, Happy Hacking!
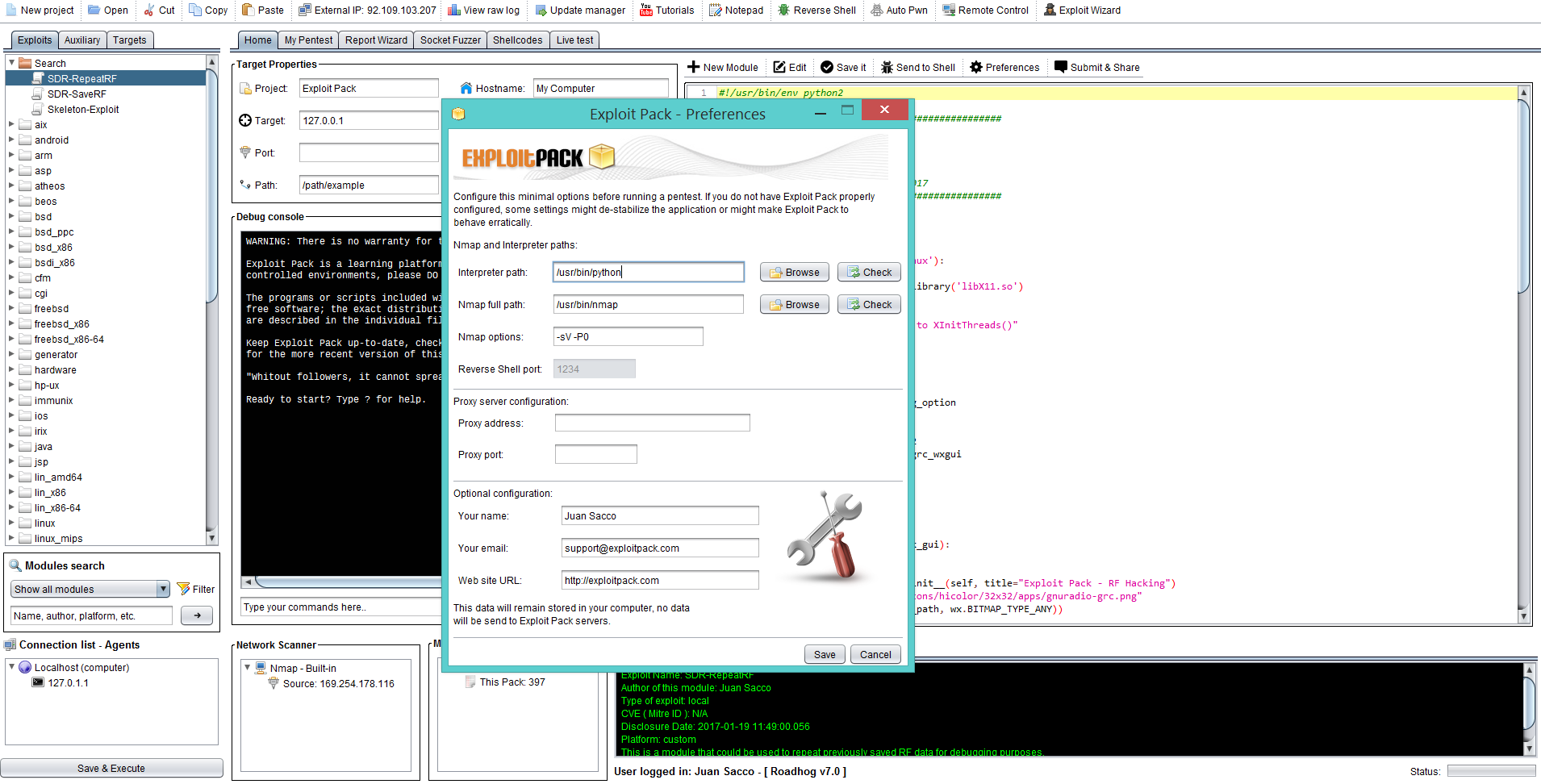
One of the first thing to setup before starting to use Exploit Pack will be to configure your preferences, the main ones that are needed ( Not optional! ) are the following:
- Interpreter path: This will be the default interpreter you will use if the exploit itself does not specify one this one will be selected by the tool, if you are unsure about which one to use we recommend you to use Python! Feel free to use Ruby, Perl, Bash, Powershell or the one you like the most.
- Nmap path and options: Here you have to configure the full path used by Nmap and the desired options you wish to use within Exploit Pack ( this options will be used when you launch the Auxiliary module "Scanner" ).
On both cases, it should be pretty straight forward just click on the button "Browse" and navigate until you found the needed binary, then click if you wish to, click on "Check" to verify if it was configured properly. After this step you will need to restart Exploit Pack for this changes to take effect.
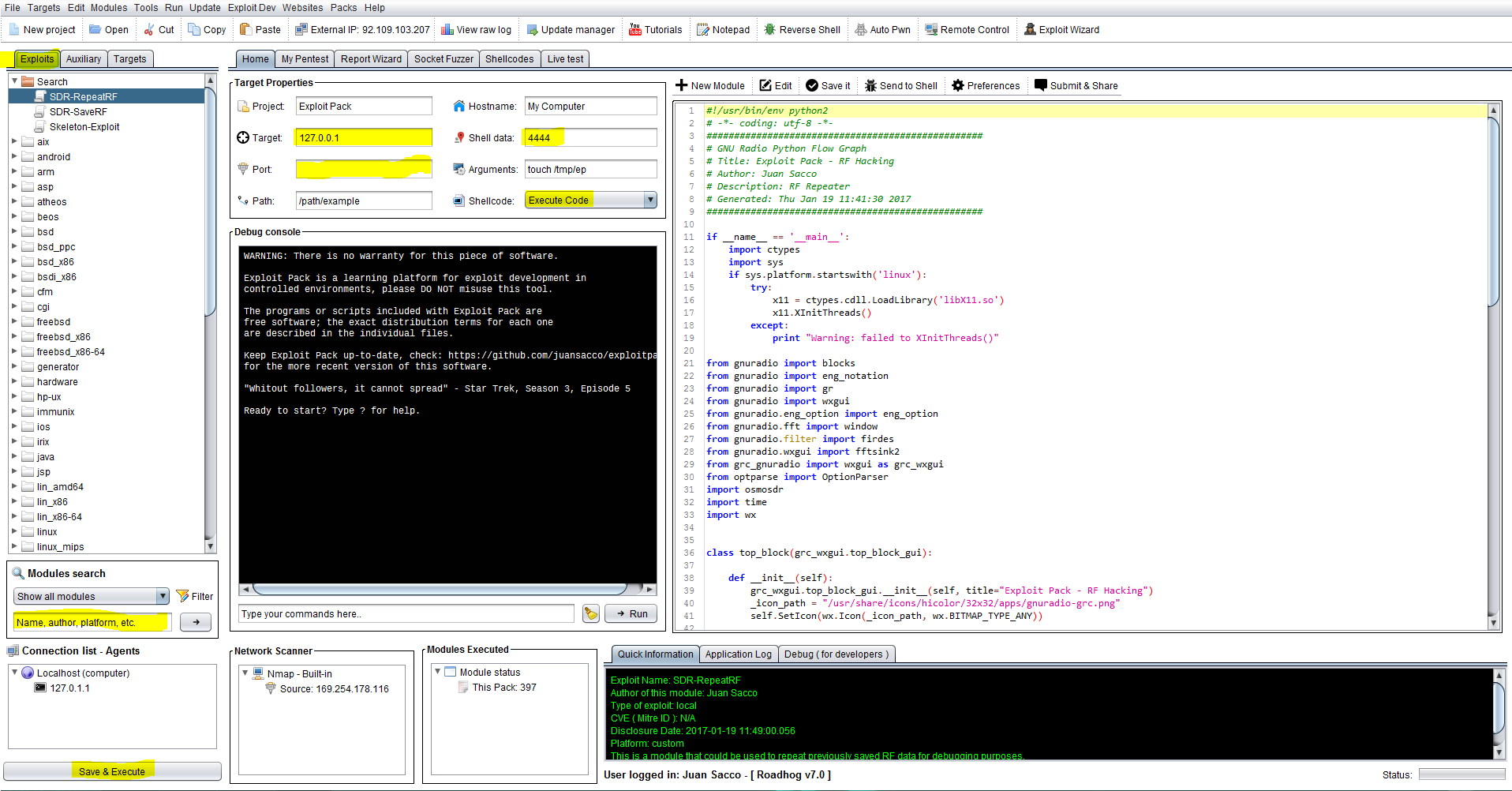
Hey you're doing great! Now we have Exploit Pack running and properly configured in your system, before executing a module let's get familiar with the tool.
As you can see in the following screenshot, there are modules, tabs and a search box, an editor and more.. It could get pretty confusing at the begging but don't stress out, we have think about it and tried to make it easier for you. Enjoy the ride, you will never be in the same stage as you are now.
- The Exploits tab and the Module search ( Left part of the screen )
This tab will help you choose by platform the exploit you need at that time, well yes! There are a lot of platforms out there! If you re using the open source version without a Pack then you will have a small amount of Exploits something around 400+ modules, there is also an editor you can use to include your owns or import what's needed at the time.
Use the search box to filter by name, platform, service, cve or any data available in the exploit module preferences. There is also a filter with some basic conditions, feel free to mix those with your own text-search.
- Target Properties ( Middle of the screen on top )
These are the properties you have to configure for the desired exploit module before executing it, some of them will get populated directly from the preferences of the exploit, but of course, you can change them for the one you need. Once you feel the options are set properly for that exploit then click on "Save & Execute" to as the button claims, save the current exploit if there was any change on it on the editor window and run it using the properties you have configured.